Oops,
It seems that we are still on Npcap 0.995:
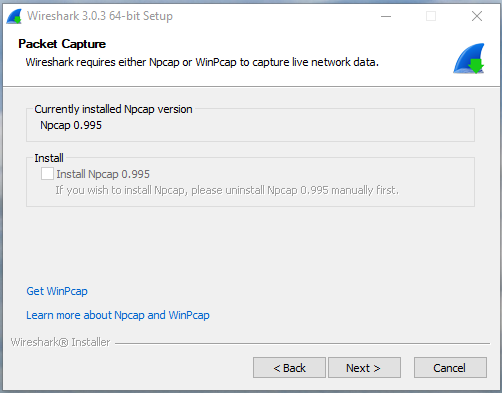
Well. It happens.
| |  |
| | | | +31 15 888 0 345 | | | hugo.van.der.kooij@xxxxxxxxx | Delft | Delftechpark 35‑37
| | |  | | | |
|
|
The information transmitted is intended only for use by the addressee and may contain confidential and/or privileged
material. Any review, re‑transmission, dissemination or other use of it, or the taking of any action in reliance upon this
information by persons and/or entities other than the intended recipient is prohibited. If you received this in error,
please inform the sender and/or addressee immediately and delete the material. Thank you.
|
From: Wireshark-announce <wireshark-announce-bounces@xxxxxxxxxxxxx> On Behalf Of Wireshark announcements
Sent: Wednesday, 17 July 2019 21:00
To: wireshark-announce@xxxxxxxxxxxxx; Community support list for Wireshark <wireshark-users@xxxxxxxxxxxxx>; Developer support list for Wireshark <wireshark-dev@xxxxxxxxxxxxx>
Subject: [Wireshark-announce] Wireshark 3.0.3 is now available
I'm proud to announce the release of Wireshark 3.0.3.
What is Wireshark?
Wireshark is the world’s most popular network protocol analyzer. It is
used for troubleshooting, analysis, development and education.
What’s New
• The Windows installers now ship with Qt 5.12.4. They previously
shipped with Qt 5.12.3.
• The Windows installers now ship with Npcap 0.996. They previously
shipped with Npcap 0.995.
• The macOS installer now ships with Qt 5.12.4. It previously
shipped with Qt 5.12.1.
Bug Fixes
The following vulnerabilities have been fixed:
• wnpa-sec-2019-20[1] ASN.1 BER and related dissectors crash. Bug
15870[2]. CVE-2019-13619[3].
The following bugs have been fixed:
• "ninja install" installs help/https://linkprotect.cudasvc.com/url?a=https%3a%2f%2ffaq.py&c=E,1,58KiIurwfM0nCQ4wOrywH-WYrYKTAxSbJUYJ99CN-OISKEvjxFaHO4N54EN8VKwrCsgRv8Dlq-DJ5N4wM5WkeyQP92GwBbz-uG5n-aZWgVAOc7YU&typo=1 instead of
help/faq.txt. Bug
15543[4].
• In Wireshark 3.0, encrypted DOCSIS PDU packets no longer match
the filter "eth.dst". Bug 15731[5].
• Developer’s Guide section 3.9 "Contribute your changes" should
incorporate or link "Writing a good commit message" from the
Wiki. Bug 15752[6].
• RSL dissector bugs in presence of optional IEs. Bug 15789[7].
• The "Media Attribute Value" field is missed in rtcp SDP
dissection (packet-sdp.c). Bug 15791[8].
• BTLE doesn’t properly detect start fragment of L2CAP PDUs. Bug
15807[9].
• Wi-SUN FAN decoder error, Channel Spacing and Reserved fields are
swapped. Bug 15821[10].
• tshark: Display filter error message references "-d" when it
should reference "-Y". Bug 15825[11].
• Open "protocol" preferences … does not work for protocol in
subtree. Bug 15836[12].
• Problems with sshdump "Error by extcap pipe: sh: sudo: command
not found". Bug 15845[13].
• editcap won’t change encapsulation type when writing pcap format.
Bug 15873[14].
• ITU-T G.8113.1 MPLS-TP OAM CC,LMM,LMR,DMM and DMR are not seen in
the 3.0.2. Bug 15887[15].
New and Updated Features
There are no new features in this release.
New Protocol Support
There are no new protocols in this release.
Updated Protocol Support
AERON, ASN.1, BTLE, CUPS, DNS, DOCSIS, DPNSS, GSM RLC/MAC, HiQnet,
ISO 14443, ISObus VT, LDAP, MAC LTE, MIME multipart, MPLS, MQ, RSL,
SDP, SMB, TNEF, and Wi-SUN
New and Updated Capture File Support
Ascend
New and Updated Capture Interfaces support
There is no new or updated capture file support in this release.
Getting Wireshark
Wireshark source code and installation packages are available from
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fwww.wireshark.org%2fdownload.html&c=E,1,lSZhRBeT9OjyJDRX3OX-YStDbOzQDmTQglMdUDtdIgQuv9aj8rY9vtoy1YnCnBM34hac63Cu_pPpQF7zLV1xY4xYtSqrvE1qFe0qn2RkjGhrnc9MTCHGOeA,&typo=1[16].
Vendor-supplied Packages
Most Linux and Unix vendors supply their own Wireshark packages. You
can usually install or upgrade Wireshark using the package management
system specific to that platform. A list of third-party packages can
be found on the download page[17] on the Wireshark web site.
File Locations
Wireshark and TShark look in several different locations for
preference files, plugins, SNMP MIBS, and RADIUS dictionaries. These
locations vary from platform to platform. You can use About→Folders to
find the default locations on your system.
Getting Help
The User’s Guide, manual pages and various other documentation can be
found at
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fwww.wireshark.org%2fdocs%2f&c=E,1,eEbC5dfQRAFx1qk66tujxcefVQBgS2YMt3goIUZY-qOZuyUzblus5fCjJ1KzF8BwLt4XDrIZNAd264oAqN_D8WfyBXuS0katJyDG2BV0vpUWTGQyRPxlBLZFpmk,&typo=1[18]
Community support is available on Wireshark’s Q&A site[19] and on the
wireshark-users mailing list. Subscription information and archives
for all of Wireshark’s mailing lists can be found on the web site[20].
Bugs and feature requests can be reported on the bug tracker[21].
Official Wireshark training and certification are available from
Wireshark University[22].
Frequently Asked Questions
A complete FAQ is available on the Wireshark web site[23].
Last updated 2019-07-17 17:31:51 UTC
References
1.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fwww.wireshark.org%2fsecurity%2fwnpa-sec-2019-20&c=E,1,1ggpBk0Ua6LhWLN8OePCsBLtUd2SeVydn4GKg0Lm388leP_UZ5lt7J7xDVfsjY1jmYkehCKamdLD_T0utCx85QkvjSzbRZAh3AkRJ1CigHZx2l0P&typo=1
2.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fbugs.wireshark.org%2fbugzilla%2fshow_bug.cgi%3fid%3d15870&c=E,1,EVofcGKBg82sVYM-GKVb8LlT4U_YMBCQJARqEaYUxxtazxPUmhr4pCKX9U3RPi8a0HawWHJuzCu21jWmQ_NaW8yKHfV96DfATLuQQUQH8SrXO3beWw,,&typo=1
3.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fcve.mitre.org%2fcgi-bin%2fcvename.cgi%3fname%3dCVE-2019-13619&c=E,1,9pgBWrVFB1rs5gD2PnuA7OrvBc-bOwIqyZK5DuD8MMFfUWelpMQPIeRO25sH4BONxfZu0e2UkND7aiWFMsrcRYs3qG5sWOE_LULFmnLAd8WQiKm-D9WSgas,&typo=1
4.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fbugs.wireshark.org%2fbugzilla%2fshow_bug.cgi%3fid%3d15543&c=E,1,LJRvxuitxn1QvthOSKFPEa1_mJuqkMDfZOAX2AwIwwqRkj6m3BaDqPuYIDlJShbRasZEvv0hhUtLhipFgAPBF5r4e25XMvQOx-i50V7Z1y-AynauVHhHjMEk-1o,&typo=1
5.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fbugs.wireshark.org%2fbugzilla%2fshow_bug.cgi%3fid%3d15731&c=E,1,e4qfFqhcWMvRIsrR4Gds97iG7LD3xIM_jzGSAV-0bBFGhPxzI4cUPHrRya9ln-2iaj7hp0JOC4f7tBRhvYY2MKBBigbssqr-0r7Z9JhC6BUdhmoQQntleQ,,&typo=1
6.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fbugs.wireshark.org%2fbugzilla%2fshow_bug.cgi%3fid%3d15752&c=E,1,6qNXCgUDVFvDyHx-JUbo32nB-UTjiqFI_BxwYdHA1R0AlH_w92Pe3Hh1U3NqzEDBzLn-61EtLhZU0G_rXY2yXYCOpt0O9OGOwQI10JSHoPU-A6aooSp3Enr4sQ,,&typo=1
7.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fbugs.wireshark.org%2fbugzilla%2fshow_bug.cgi%3fid%3d15789&c=E,1,f33R9bpL8ziWlzjzLVraC6sMz2dAHlHmLI2Ht5qdNN7XEbglZ28iRz6DzbB4kf5eRMSkhpqpynIHEWytXA7zG14W7Ynx3DPZpvgPeiFocR0,&typo=1
8.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fbugs.wireshark.org%2fbugzilla%2fshow_bug.cgi%3fid%3d15791&c=E,1,5SYyf2YaPJZBDY485VBgUJ3YL3hiwwW83en8qTTzT8SJWVMJ2D_pJhXJJ7GYOiXgDBlVpJimST8VhN1JMJFn0z5F6Jn904Ebh7pR95MuR_tLB6jZJiA_g5X7Z3uj&typo=1
9.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fbugs.wireshark.org%2fbugzilla%2fshow_bug.cgi%3fid%3d15807&c=E,1,ekUlaSj-GU_VZ5vjjAN20sudZLKJYN5FFfdRz34YRPjIhHp_jPcrFSO-au7kq_EkqAsDZ69Oifwf34cEiN5cAzjBwcjB_IQb6vHVOsvQ&typo=1
10.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fbugs.wireshark.org%2fbugzilla%2fshow_bug.cgi%3fid%3d15821&c=E,1,yp5NaeDEr2jJFXUaKgJdTNgfDOoXQlrHw_6KuZkB8r6hw1e9m4R5CBP3TeQMkAnm0zOaYefjWk5Q-cElweU0BRiyEJagPaf7yp3Mo8NxP0R7T2ilvY7K_bk,&typo=1
11.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fbugs.wireshark.org%2fbugzilla%2fshow_bug.cgi%3fid%3d15825&c=E,1,BG9-dsNaqq4iKRVZ5YZaAJZ3kIOMW9bg3zFIKWt8HnuSGaJtgU_hkuQC_ngCd1O0cKMBGJLISETw74nWNTmGh3FwmbukLbs5d2Xp0qdutSW6jYm-Hg,,&typo=1
12.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fbugs.wireshark.org%2fbugzilla%2fshow_bug.cgi%3fid%3d15836&c=E,1,4dL6AxJMMgy2KjDV-JR7VxvnVYiUw5hP9Eu6oj71b2XceT5vyDyB5Cf-qbrOba0PXmL8Q8wccLFhI7GO4VcGp-f_GkjiyJmp_YZPD1bDgKQWWIhmsRoW8ro5oURL&typo=1
13.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fbugs.wireshark.org%2fbugzilla%2fshow_bug.cgi%3fid%3d15845&c=E,1,KzOzS5TQ7pCdPMhHHfmVhmxOmpkepgvZz5sq9wrTakUVaF7dcHeiEjCTad74PAVOYNvJpXquFjJ2RtnDPsf2V7jVcwdl9vjTX8bHbqTJfA,,&typo=1
14.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fbugs.wireshark.org%2fbugzilla%2fshow_bug.cgi%3fid%3d15873&c=E,1,B_Bdy2dhQoTkeaazXYvODTlkVc3hGd39cEYzwuOCHTI-DZsUObb_tkkE4DLzgVK7DdmHdOxGRDPtEphXdGK5Yvr-a6Fz4ddKwu85LZG-WnAta5zcpRSb2gM,&typo=1
15.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fbugs.wireshark.org%2fbugzilla%2fshow_bug.cgi%3fid%3d15887&c=E,1,Wvfuo7OwO9X2wzjBJ2glSt0Fkj4eqb4l8esifWrQK69bVpWL6kBLakQ3h_9cDVz0etCGU4s9n0-nDVUbGOmcVR2DmZGxzxc_Xi7Y5K-4em0fwPd2J-s,&typo=1
16.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fwww.wireshark.org%2fdownload.html&c=E,1,W7N2IxmBU-NXMeaNmdyctKqpZ9ULt3YHNJOmFb92zaxJdo-zpoXJcb6Oi31bdWze8Rn6g1qnCwBhHb6AhxekrT9o8wszTG-BogQVUe0VMA6jMrl_PvujOen0BFlz&typo=1
17.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fwww.wireshark.org%2fdownload.html%23thirdparty&c=E,1,Vwyn4E8G0BOL8cJrPL1YV3aXRpOvIf7v2m1h-HPycBivDvV3BF39khLULyO3PERyn3N3MX9jDHUq0QTocUS5jEm4p5ZY9PHh-lGgDVa8qCxX&typo=1
18.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fwww.wireshark.org%2fdocs%2f&c=E,1,tbmm3gobvxg4HOviWyzXrJ-_SXmpVj6VibCQooVcMCu038iPdTNi5nDpnkcg7JTaFVNkDWVrcQUHB7KBLQt8DRd07jSE-J4b3jhRGlJaok6Zlo222rc,&typo=1
19.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fask.wireshark.org%2f&c=E,1,CCjvheFmwCEzh-O7_m-XvZgWkPl9NWMEFvj4yYQHfJrqwbhUACUpL_Zf21CSg3eDkgd27_jO6ADEIKEtXiQ0uzdOhZbbcdsaVyqNUrP9QMIu1hojGCI9jXrpLw,,&typo=1
20.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fwww.wireshark.org%2flists%2f&c=E,1,mcg4HEgidrS5UC__bAyqJ9mhpweYTUO2UGoOS_AmtWG-MnfNSZbiedvT26Ds29xUrYxUXklOsP87JkE5MuEKXOXuFc_gz-ZL5buUHDZDrxGC8lG_vW7_0-D6MZA,&typo=1
21.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fbugs.wireshark.org%2f&c=E,1,RlE_GIAu6U2y2cVUMq3ZCmf7RUAvkP4kKu3WHcBJUQ8gDmUrXCFf7lGvTIvORe6rEnDah4Cv4Afi9iOFKNGfrUSvNXvFPHhAJpyd3raQF3ACfsKBvlM9HcMHh4A,&typo=1
22.
https://linkprotect.cudasvc.com/url?a=http%3a%2f%2fwww.wiresharktraining.com%2f&c=E,1,7r9fbtzSryAGR9BgHoeFiyQJGSi4nPCx1whcROif0XDUVcUyKreRoc0GyOMFOIDASYLmhHFBVOJzA0HHI4Ee7tpNNEcAnpwwO3RA9mqqpTgcmarCDZtmn3M,&typo=1
23.
https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fwww.wireshark.org%2ffaq.html&c=E,1,-P6jzb-MG4iQo0cPkIbuAUrx3DhM1x7gHbjepw46vnfR3Yyiwx9jHsRSaxn3Npig7KCDteh_terlpGbH0asU-TK8tIvmYh221ACV1i0DSy-L-rd1PPru2-0AIsP1&typo=1
Digests
wireshark-3.0.3.tar.xz: 30923980 bytes
SHA256(wireshark-3.0.3.tar.xz)=af92729c781d870110885c31ebcbe4c4224ed51bb580d00c896fe9746994211c
RIPEMD160(wireshark-3.0.3.tar.xz)=4ccaf1702977f7ffb225896f90807a35dd6e33cc
SHA1(wireshark-3.0.3.tar.xz)=3a7406d54de9fd925a3d9800471610144fe44354
Wireshark-win64-3.0.3.exe: 59321664 bytes
SHA256(Wireshark-win64-3.0.3.exe)=824cbeeb48ed720a24b70725cb8db2353ed331e05f3d0a832ff96acb02292d62
RIPEMD160(Wireshark-win64-3.0.3.exe)=6f8c4dad7006958441d824098a2d5475be421533
SHA1(Wireshark-win64-3.0.3.exe)=9e5f39adaa22e4016d0cba93a6e9f302d91cc313
Wireshark-win32-3.0.3.exe: 54140848 bytes
SHA256(Wireshark-win32-3.0.3.exe)=9e276aff3164e98293d478758542855bdfb7ffd295156f4d5011ba76a9cbf814
RIPEMD160(Wireshark-win32-3.0.3.exe)=c30b2818d3f5478dd0175ec739b6bb3d0c6679b0
SHA1(Wireshark-win32-3.0.3.exe)=b0fd5c543421844a8a33fa00d0594dddc5572045
Wireshark-win32-3.0.3.msi: 42061824 bytes SHA256(Wireshark-win32-3.0.3.msi)=d220bb9459dd9dcd2eb572a112a57069d7fbe18979352a8047493bd22e9dda7b
RIPEMD160(Wireshark-win32-3.0.3.msi)=537efd1483dfcae936832017aa288e79f2f04d29
SHA1(Wireshark-win32-3.0.3.msi)=1f81dfafc3481a32f8f15f4c3f6c39f831f6e4b3
Wireshark-win64-3.0.3.msi: 47251456 bytes
SHA256(Wireshark-win64-3.0.3.msi)=9ede8409906f4830f8d9c442fd884989eac4cfc942080c73ad7b4e272c00d081
RIPEMD160(Wireshark-win64-3.0.3.msi)=e160af727a48c360011ce03de061041dc1e65826
SHA1(Wireshark-win64-3.0.3.msi)=56e258f093d4455cedc82b6d93201ea478a748f2
WiresharkPortable_3.0.3.paf.exe: 35834584 bytes
SHA256(WiresharkPortable_3.0.3.paf.exe)=f1c9ceed2eacf23bc842611ab1b11280ea850bdbc4211ec5b8de6ddce5615dd9
RIPEMD160(WiresharkPortable_3.0.3.paf.exe)=3d86c378b0994e9de4f777c45a082355107594d8
SHA1(WiresharkPortable_3.0.3.paf.exe)=f15116f2e179acc6ce40669ca478477525e1c14a
Wireshark 3.0.3 Intel 64.dmg: 93069527 bytes SHA256(Wireshark 3.0.3 Intel
64.dmg)=71d0196e7368715958598c8286f5219eb24fad08acf1cfe9186ef19d29e04ae9
RIPEMD160(Wireshark 3.0.3 Intel
64.dmg)=1cfe89e437765afe0843cea54d670401fe0d5831
SHA1(Wireshark 3.0.3 Intel 64.dmg)=78490223d3894cd90369aaab430ba4b66d42eba5
You can validate these hashes using the following commands (among others):
Windows: certutil -hashfile Wireshark-win64-x.y.z.exe SHA256
Linux (GNU Coreutils): sha256sum wireshark-x.y.z.tar.xz
macOS: shasum -a 256 "Wireshark x.y.z Intel 64.dmg"
Other: openssl sha256 wireshark-x.y.z.tar.xz


