Thanks for everyone’s responses.
Obviously the more we strip out, the less useful is the
information, but to be able to get the capture from the customer we need to
anonymise the IPs and strip out the payload as a minimum requirement – that would
probably get approved by their security people.
In terms of ‘what is the payload?’. In the following example
(Sky Player from an Xbox), we just need the first 4 sections, not the HTTP
content in the last (5th) section:
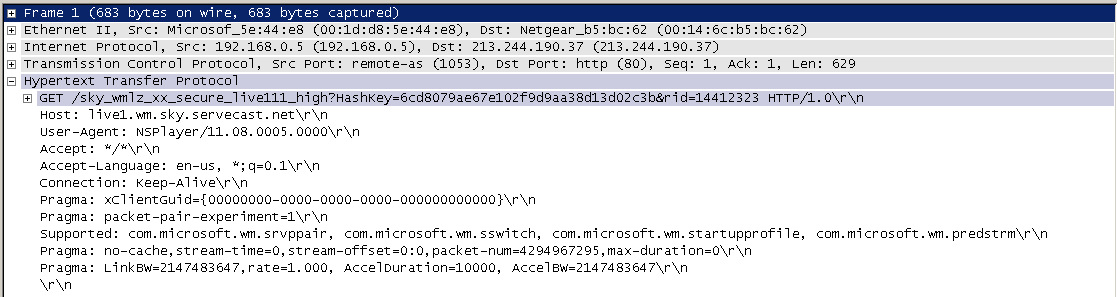
And anonymising would mean allocating a random, but consistent
alternate IP, e.g. 213.244.190.37 would always be 20.67.1.192, but this would
be randomly selected by the Anonymiser (new super-hero!).
Cheers,
Dave
From: wireshark-users-bounces@xxxxxxxxxxxxx
[mailto:wireshark-users-bounces@xxxxxxxxxxxxx] On Behalf Of Martin
Visser
Sent: 30 November 2009 02:17
To: Community support list for Wireshark
Cc: JONES IAN D; MAGNIES Nicolas
Subject: Re: [Wireshark-users] Saving without payload
I guess the question any one will ask "What is the
definition of payload?". One man's header is another man's data. I
f you want to properly obfuscate your capture data you would
want to jitter your timestamps (so people don't know when you are sending),
change your IP address (as you already indicated), translate or zero your TCP
and UDP ports (so baddies don't know what protocol your sending), and zero or
at least transmogrify segment/datagram contents. But of course then you
possibly have little use of what you had captured.
Regards, Martin
MartinVisser99@xxxxxxxxx
On Fri, Nov 27, 2009 at 11:22 PM, WATT DAVE <Dave.Watt@xxxxxxxxxxxxxxxxxx>
wrote:
We have a high
priority requirement to
save the capture,
stripping out ALL payload bytes. This is for UK legal compliance
when analysing traffic
subject to data protection.
I can easily just
capture the first 68
bytes of each packet, but that will sometimes include the first part of the
payload.
Ideally, we want to
capture everything and then save only the headers.
We would also like to
be able to ‘anonymise’
the IP addresses during the save.
Can Wireshark do any of this?
It would seem to be a useful feature required in many countries where such data
protection is in place.
Without doing this we
cannot mail the
capture file to R&D for investigation, in fact we cannot even save the capture to a local disk.
___________________________________________________________________________
Sent via: Wireshark-users mailing list <wireshark-users@xxxxxxxxxxxxx>
Archives: http://www.wireshark.org/lists/wireshark-users
Unsubscribe: https://wireshark.org/mailman/options/wireshark-users
mailto:wireshark-users-request@xxxxxxxxxxxxx?subject=unsubscribe

