Wireshark can read in a hex dump and write the data described into a temporary libpcap capture file. It can read hex dumps with multiple packets in them, and build a capture file of multiple packets. It is also capable of generating dummy Ethernet, IP and UDP, TCP, or SCTP headers, in order to build fully processable packet dumps from hexdumps of application-level data only. Alternatively a Dummy PDU header can be added to specify a dissector the data should be passed to initially.
Two methods for converting the input are supported:
Wireshark understands a hexdump of the form generated by od -Ax -tx1 -v. In
other words, each byte is individually displayed and surrounded with a space.
Each line begins with an offset describing the position in the packet, each
new packet starts with an offset of 0 and there is a space separating the
offset from the following bytes. The offset is a hex number (can also be octal
or decimal), of more than two hex digits.
Here is a sample dump that can be imported:
000000 00 e0 1e a7 05 6f 00 10 ........ 000008 5a a0 b9 12 08 00 46 00 ........ 000010 03 68 00 00 00 00 0a 2e ........ 000018 ee 33 0f 19 08 7f 0f 19 ........ 000020 03 80 94 04 00 00 10 01 ........ 000028 16 a2 0a 00 03 50 00 0c ........ 000030 01 01 0f 19 03 80 11 01 ........
There is no limit on the width or number of bytes per line. Also the text dump at the end of the line is ignored. Byte and hex numbers can be uppercase or lowercase. Any text before the offset is ignored, including email forwarding characters >. Any lines of text between the bytestring lines are ignored. The offsets are used to track the bytes, so offsets must be correct. Any line which has only bytes without a leading offset is ignored. An offset is recognized as being a hex number longer than two characters. Any text after the bytes is ignored (e.g. the character dump). Any hex numbers in this text are also ignored. An offset of zero is indicative of starting a new packet, so a single text file with a series of hexdumps can be converted into a packet capture with multiple packets. Packets may be preceded by a timestamp. These are interpreted according to the format given. If not the first packet is timestamped with the current time the import takes place. Multiple packets are written with timestamps differing by one nanosecond each. In general, short of these restrictions, Wireshark is pretty liberal about reading in hexdumps and has been tested with a variety of mangled outputs (including being forwarded through email multiple times, with limited line wrap etc.)
There are a couple of other special features to note. Any line where the first
non-whitespace character is # will be ignored as a comment. Any line beginning
with #TEXT2PCAP is a directive and options can be inserted after this command to
be processed by Wireshark. Currently there are no directives implemented. In the
future these may be used to give more fine grained control on the dump and the
way it should be processed e.g. timestamps, encapsulation type etc.
Wireshark is also capable of scanning the input using a custom perl regular
expression as specified by GLib’s GRegex here.
Using a regex capturing a single packet in the given file
wireshark will search the given file from start to the second to last character
(the last character has to be \n and is ignored)
for non-overlapping (and non-empty) strings matching the given regex and then
identify the fields to import using named capturing subgroups. Using provided
format information for each field they are then decoded and translated into a
standard libpcap file retaining packet order.
Note that each named capturing subgroup has to match exactly once a packet, but they may be present multiple times in the regex.
For example the following dump:
> 0:00:00.265620 a130368b000000080060 > 0:00:00.280836 a1216c8b00000000000089086b0b82020407 < 0:00:00.295459 a2010800000000000000000800000000 > 0:00:00.296982 a1303c8b00000008007088286b0bc1ffcbf0f9ff > 0:00:00.305644 a121718b0000000000008ba86a0b8008 < 0:00:00.319061 a2010900000000000000001000600000 > 0:00:00.330937 a130428b00000008007589186b0bb9ffd9f0fdfa3eb4295e99f3aaffd2f005 > 0:00:00.356037 a121788b0000000000008a18
could be imported using these settings:
regex: ^(?<dir>[<>])\s(?<time>\d+:\d\d:\d\d.\d+)\s(?<data>[0-9a-fA-F]+)$ timestamp: %H:%M:%S.%f dir: in: < out: > encoding: HEX
Caution has to be applied when discarding the anchors ^ and $, as the input
is searched, not parsed, meaning even most incorrect regexes will produce valid
looking results when not anchored (however anchors are not guaranteed to prevent
this). It is generally recommended to sanity check any files created using
this conversion.
Supported fields:
-
data: Actual captured frame data
The only mandatory field. This should match the encoded binary data captured and is used as the actual frame data to import.
-
time: timestamp for the packet
The captured field will be parsed according to the given timestamp format into a timestamp.
If no timestamp is present an arbitrary counter will count up seconds and nanoseconds by one each packet.
-
dir: the direction the packet was sent over the wire
The captured field is expected to be one character in length, any remaining characters are ignored (e.g. given "Input" only the 'I' is looked at). This character is compared to lists of characters corresponding to inbound and outbound and the packet is assigned the corresponding direction. If neither list yields a match, the direction is set to unknown.
If this field is not specified the entire file has no directional information.
-
seqno: an ID for this packet
Each packet can be assigned a arbitrary ID that can used as field by Wireshark. This field is assumed to be a positive integer base 10. This field can e.g. be used to reorder out of order captures after the import.
If this field is not given, no IDs will be present in the resulting file.
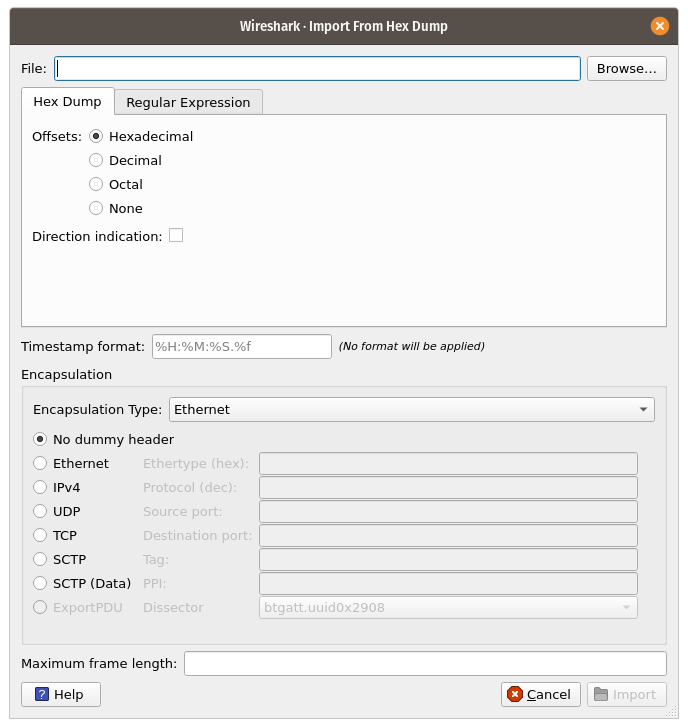
This dialog box lets you select a text file, containing a hex dump of packet data, to be imported and set import parameters.
Specific controls of this import dialog are split in three sections:
- File Source
- Determine which input file has to be imported
- Input Format
- Determine how the input file has to be interpreted.
- Encapsulation
- Determine how the data is to be encapsulated.
- Filename / Browse
- Enter the name of the text file to import. You can use Browse to browse for a file.
This section is split in the two alternatives for input conversion, accessible in the two Tabs "Hex Dump" and "Regular Expression"
In addition to the conversion mode specific inputs, there are also common parameters, currently only the timestamp format.
- Offsets
- Select the radix of the offsets given in the text file to import. This is usually hexadecimal, but decimal and octal are also supported. Select None when only the bytes are present. These will be imported as a single packet.
- Direction indication
- Tick this box if the text file to import has direction indicators before each frame. These are on a separate line before each frame and start with either I or i for input and O or o for output.
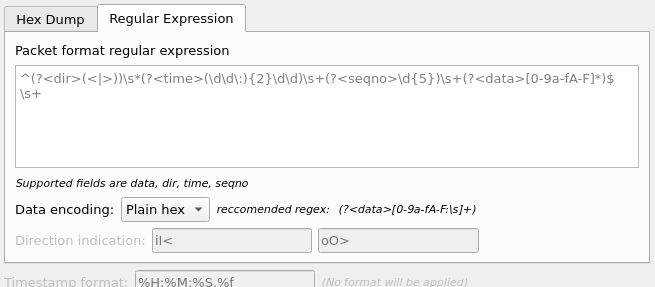
- Packet format regular expression
-
This is the regex used for searching packets and metadata inside the input file.
Named capuring subgroups are used to find the individual fields. Anchors
^and$are set to match directly before and after newlines\nor\r\n. See GRegex for a full documentation. - Data encoding
-
The Encoding used for the binary data. Supported encodings are plain-hexadecimal, -octal, -binary and base64. Plain here means no additional characters are present in the data field beyond whitespaces, which are ignored. Any unexpected characters abort the import process.
Ignored whitespaces are
\r,\n,\t,\v, ` ` and only for hex:, only for base64=.Any incomplete bytes at the field’s end are assumed to be padding to fill the last complete byte. These bits should be zero, however this is not checked.
- Direction indication
-
The lists of characters indicating incoming vs. outgoing packets. Tese fields
are only available when the regex contains a
(?<dir>…)group.
- Timestamp Format
-
This is the format specifier used to parse the timestamps in the text file to import. It uses the same format as
strptime(3)with the addition of%ffor zero padded fractions of seconds. The percision of%fis determined from it’s length. The most common fields are%H,%Mand%Sfor hours, minutes and seconds. The straightforward HH:MM:SS format is covered by %T. For a full definition of the syntax look forstrptime(3),In Regex mode this field is only available when a
(?<time>…)group is present.In Hex Dump mode if there are no timestamps in the text file to import, leave this field empty and timestamps will be generated based on the time of import.
- Encapsulation type
- Here you can select which type of frames you are importing. This all depends on from what type of medium the dump to import was taken. It lists all types that Wireshark understands, so as to pass the capture file contents to the right dissector.
- Dummy header
- When Ethernet encapsulation is selected you have to option to prepend dummy headers to the frames to import. These headers can provide artificial Ethernet, IP, UDP, TCP or SCTP headers or SCTP data chunks. When selecting a type of dummy header the applicable entries are enabled, others are grayed out and default values are used. When the Wireshark Upper PDU export encapsulation is selected the option ExportPDU becomes available. This allows you to select the name of the dissector these frames are to be directed to.
- Maximum frame length
- You may not be interested in the full frames from the text file, just the first part. Here you can define how much data from the start of the frame you want to import. If you leave this open the maximum is set to 256kiB.
Once all input and import parameters are setup click to start the import. If your current data wasn’t saved before you will be asked to save it first.
If the import button doesn’t unlock, make sure all encapsualation parameters are in the expected range and all unlocked fields are populated when using regex mode (the placeholder text is not used as default).
When completed there will be a new capture file loaded with the frames imported from the text file.